How to Enable Secure Authentication in Mobile Applications
In this article, we’ll describe common authentication types and their main weaknesses. We will also provide some insights on the most effective mechanisms and methods to implement multi-factor authentication.
Password-Based Authentication in Mobile Applications
Performing the main authentication function, login and password have become two pillars of an overall login system and the core of information security. Additional methods of identifying a user and preventing an unauthorized access usually complement this “authentication pair”. Thus, a PIN code is considered as a good protection mechanism applied to support the classic scheme of authentication, but not to fully substitute it.
But why not to remove a password field in mobile applications and apply login only? It is actually possible but not viable. To guarantee that no one figures out the user’s login and accesses private data without being noticed, some complexity will be added anyway. The reason is that we often enter logins in the request and report forms and share it with the third parties like support services. Besides, login may be required to demonstrate the account info publicly. In this case, complicated and hidden logins will not differ much from passwords because then, another field should be added, e.g. nick.
Moreover, we are more accustomed to logins and passwords than other authentication methods. First, every smartphone user has at least one pair of logins and passwords. Second, programmers often use “a password input-field” as a specific control component in each development environment that contains a password hidden under asterisks.
Although this method has ingrained in the overall authentication system as an essential one, it demonstrates serious weaknesses like password storing and sharing. At the same time, the most common preemptive ways described below cannot entirely protect the password’s integrity from new brute force or dictionary attacks.
How to Secure Authentication and Data Transmission through Encryption
Balancing Hardware and Software Encryption
With the emergence of computer networks, sharing a password openly with anyone has become threatening. Even an inept hacker could capture it and get access to the person’s data. Thus, the encryption was implemented giving rise to Digest Authentication and NTLM. Since then, data has been encoded and transmitted in more secure ways.
The importance of encryption for mobile devices has grown with the tendency of users to store confidential business data on their smartphones. According to Ponemon Institute research, 55% of surveyed respondents confirmed that confidential business documents could be accessed through their smartphones.
Therefore, mobile data encryption is applied in two main directions:
- Full encryption of stored data on the device.
- Encryption of shared data from one device to another.
To protect data on the device, both hardware encryption and software encryption are normally implemented.
Hardware encryption is based on the encoding of the entire file system (OS and user data) written to flash memory. When the data is accessed by an authorized user, the system is decoded and read to main memory. In terms of authentication, when the device is unlocked, all data and applications can be easily accessed since the system is automatically decrypted. Hence, the sensitive data in a specific application can be endangered with the low-security rate of a chosen unlock method.
In this case, software encryption can add another layer of protection safeguarding an access to business important applications like emails, confidential documents, financial files, etc. It can be used for one particular application or a group of connected apps to encrypt and decrypt selected confidential data.
Those who are seriously concerned with sensitive data transmission apart from on-device encryption can also utilize encoding of the shared data between devices. Some software providers (Symantec, Data Motion, Proofpoint) already support mobile email encryption compatible with almost all email clients. The same feature is available in iMessages that allows encrypting messages and sending them directly to the recipient.
Pros and Cons of Main Encryption Methods in the Authentication Process
Symmetric Encryption
Encoding and decoding of data are realized with the same shared key which can be any number, a meaningful word or a random string of letters and digits. Only authorized parties can have access to the key and transmitted message.
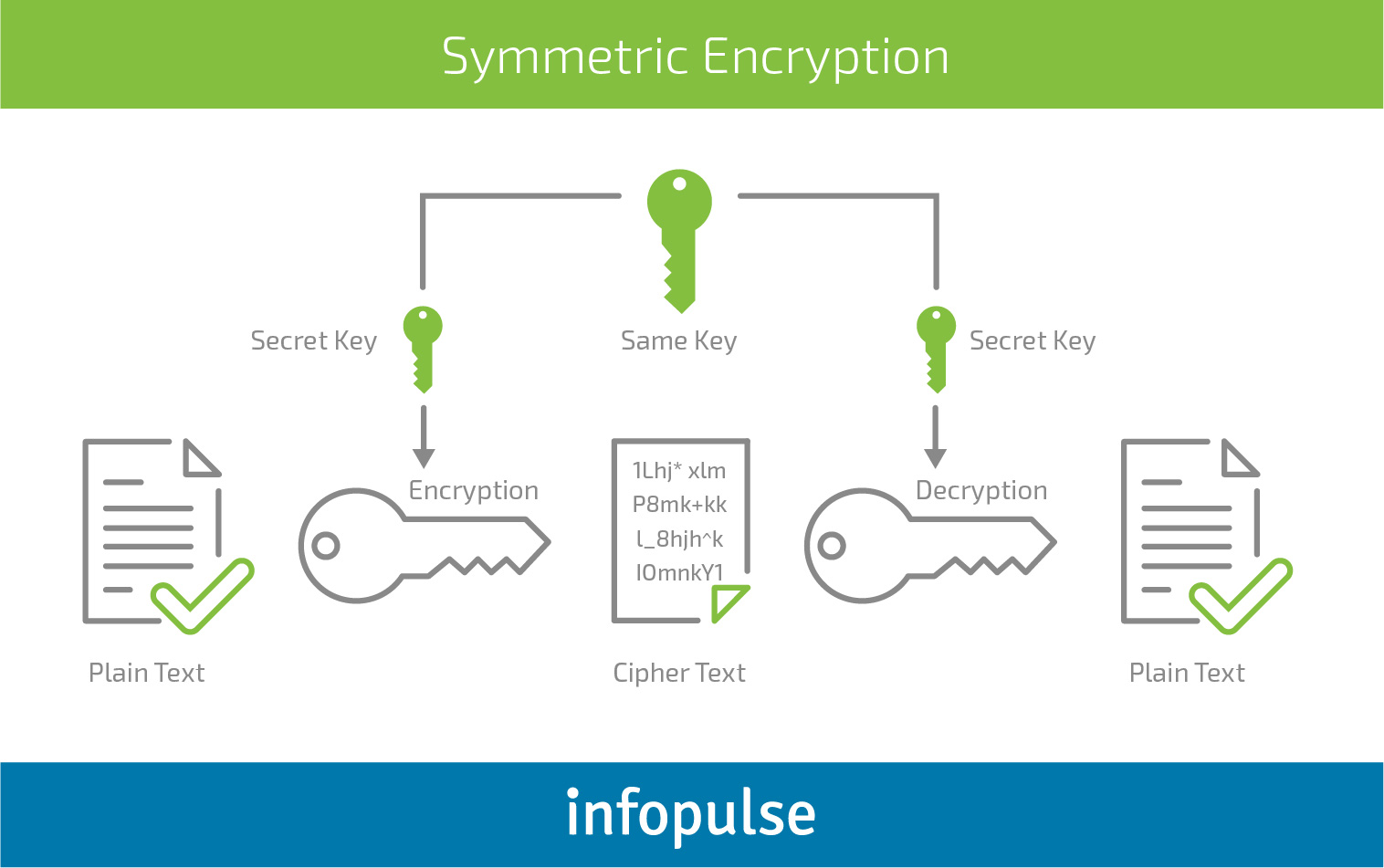
Advantages
- Rather low complexity;
- Easier to implement in hardware;
- Faster cryptography;
- Less processing power needed.
Disadvantages
- The same key is used for both encryption and decryption;
- A reliable communication channel is needed to remotely share a private key;
- A new key is created for another receiver complicating management of multiple keys.
Asymmetric Encryption
This technique is based on two different keys for encryption and decryption. A public key encrypts data, verifies a holder of a private key and establishes secure channel for the exchange. Whereas a private (aka “secret”) key decrypts data and is never shared.
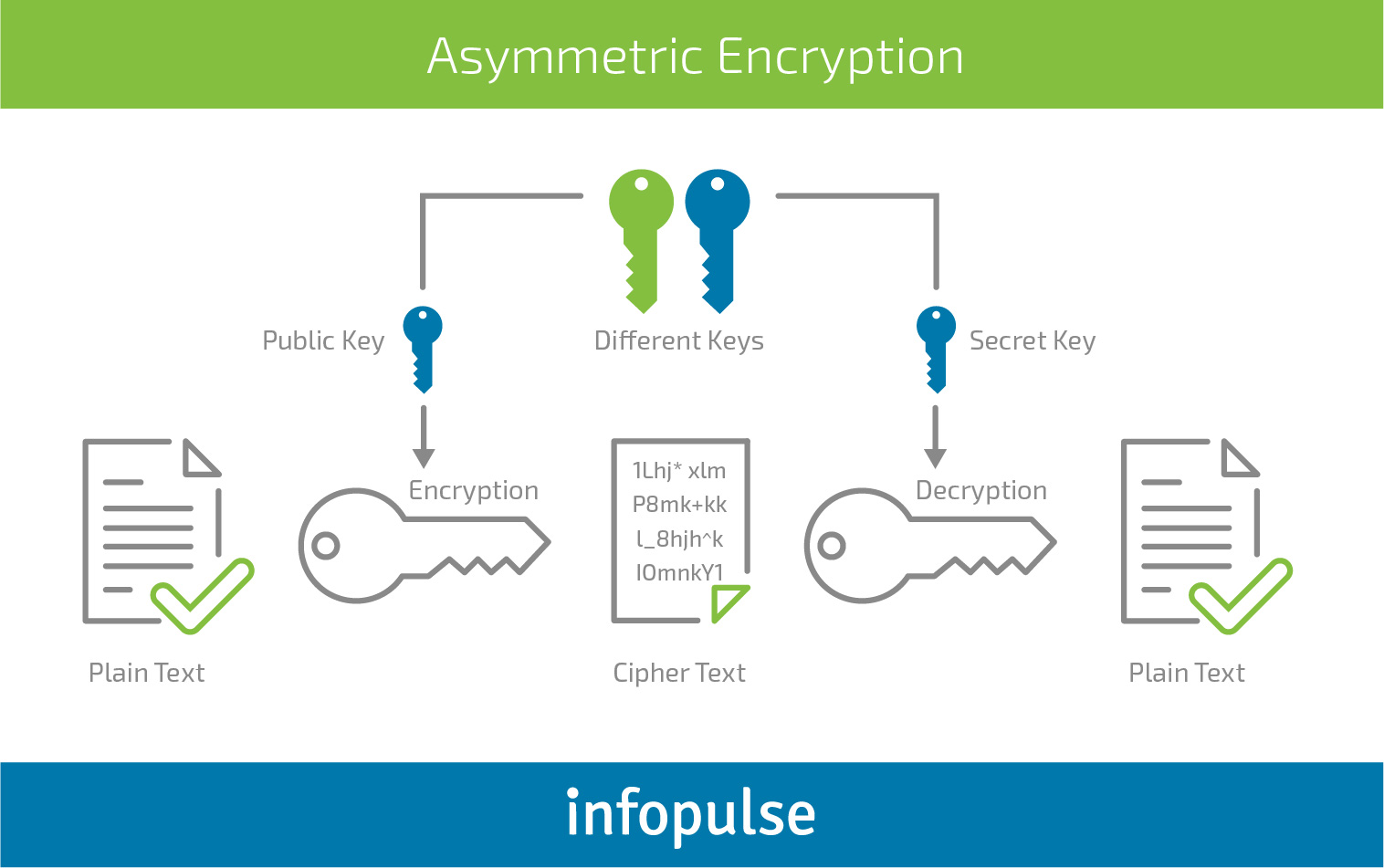
Advantages
- No need to search a secure communication channel;
- Fewer key-management issues;
- Applicable to data authentication through digital signatures.
Disadvantages
- Requires high computational power;
- More complicated and slower;
- No built-in authentication method;
- An encrypted message can be modified and compromised.
Hashing
Compared to other aforementioned encryption methods hashing is more secure. First, the hash function is based on the mathematical algorithm that makes it impossible to be altered. Second, the password is stored not as a plaintext but as a hash digest, a value represented in the alphanumeric message.
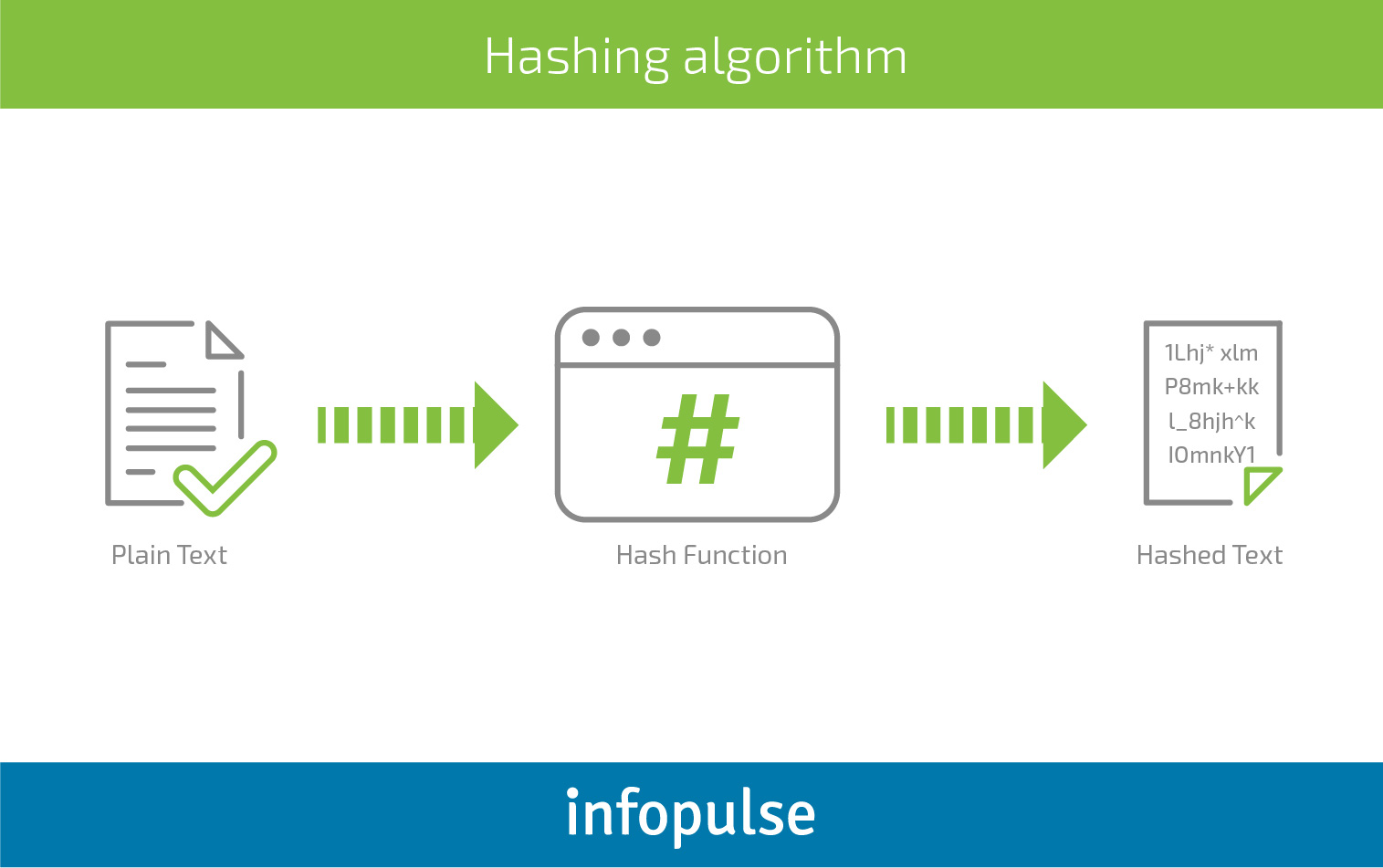
Advantages
- Authenticates a user by comparing a hashed password of a user with the stored hash;
- One-way hash function eliminates the risk of the old password being restored and obtained by a hacker.
Disadvantages
- Simple hashing of passwords can be cracked through a dictionary attack or direct access to the database of common strings.
How to Manage and Store Passwords in Mobile Applications
The growing number of applications one person used a day soon made it difficult to keep in mind multiple logins and passwords. Besides, entering an application had to be simplified to improve user experience and decrease customer attrition after a few access fails.
Today oAuth and Single-Sign-On (SSO) enable the seamless access to the same mobile application at any time the user needs.
oAuth
Instead of requesting a user to enter another pair of login and password, you can use the most common pattern of oAuth 2.0 Protocol accessing a trusted server like Google, Microsoft, Facebook, Amazon, Twitter, etc. to enable secure but simplified authentication process. The authentication begins when on behalf of a user the application requests an access token from the trusted server, e.g. Google Authorization Server. Upon receiving a token, which grants an access to particular resources or data described in the token request, the application sends it to the Authorization Server. Thus, the whole mechanism allows validating an access to the user’s credentials but not the stored password.
For more details, view the following communication flow between all the parties of the oAuth process.
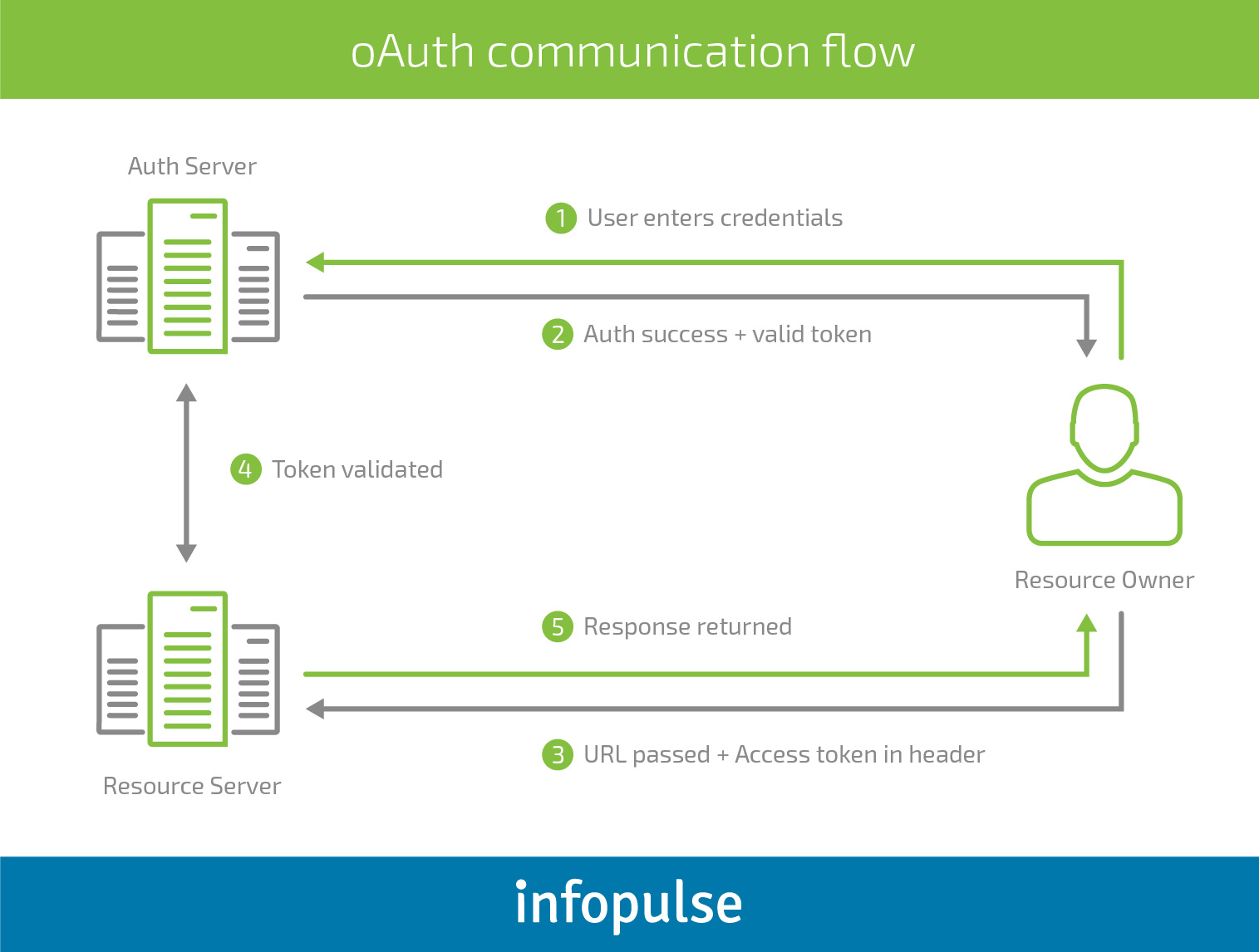
oAuth has become especially helpful for the repeated transmission of authenticating credentials. Thus, an application requests the user’s credentials with each new inquiry, which allows securing data exchange between a mobile application and a remote server.
Single-Sign-On (SSO)
Single-Sign-On (SSO) functions in a slightly different direction. For web, all applications share the user’s credentials if they are located on the same trusted server for oAuth authentication, e.g. websites with Google, Microsoft, Twitter or other accounts. It means that entering login and password in one application the user is already identified in another one.
Considering mobile applications, this approach works in the same way but with some reservations and requires additional efforts of developers.
The main difference is that the user’s credentials must be maintained on the devices to extract them when running an application next time. Other applications that share an access to these credentials will use the same extraction method for the automatic authentication.
The Place to Store Passwords
Although password storing becomes unnecessary and obsolete with the applied oAuth pattern, we should still consider the classic authentication approach and safe methods for keeping sensitive data.
Logically, the place where logins and passwords are stored must be highly secure against any potential attacks. Depending on the platform and technologies, this place can have different names, yet frequently we address it as KeyChain (iOS, Android). There, the stored data is encrypted; hence, an access to it is restricted. Most importantly, the security of this place on the device is ensured at the OS level.
Where Passwords Must Not Be Stored
Any database, as well as system log, would be the most unprotected places to store the user’s logins and passwords. Using public variables for this purpose even temporary is also unacceptable. At the moment, extracting such data from KeyChain when necessary is the best alternative.
How secure are password, PIN, and pattern against attacks?
Pattern
When users face the need to secure their corporate email system on the phone, the authentication method becomes critical. For instance, to enter Outlook email system, you will be required to choose one of mobile screen lock types if you have none. At the screenshot, you can see some lock types with their security rate. These types can be also used to safeguard the access to any critically important mobile application.
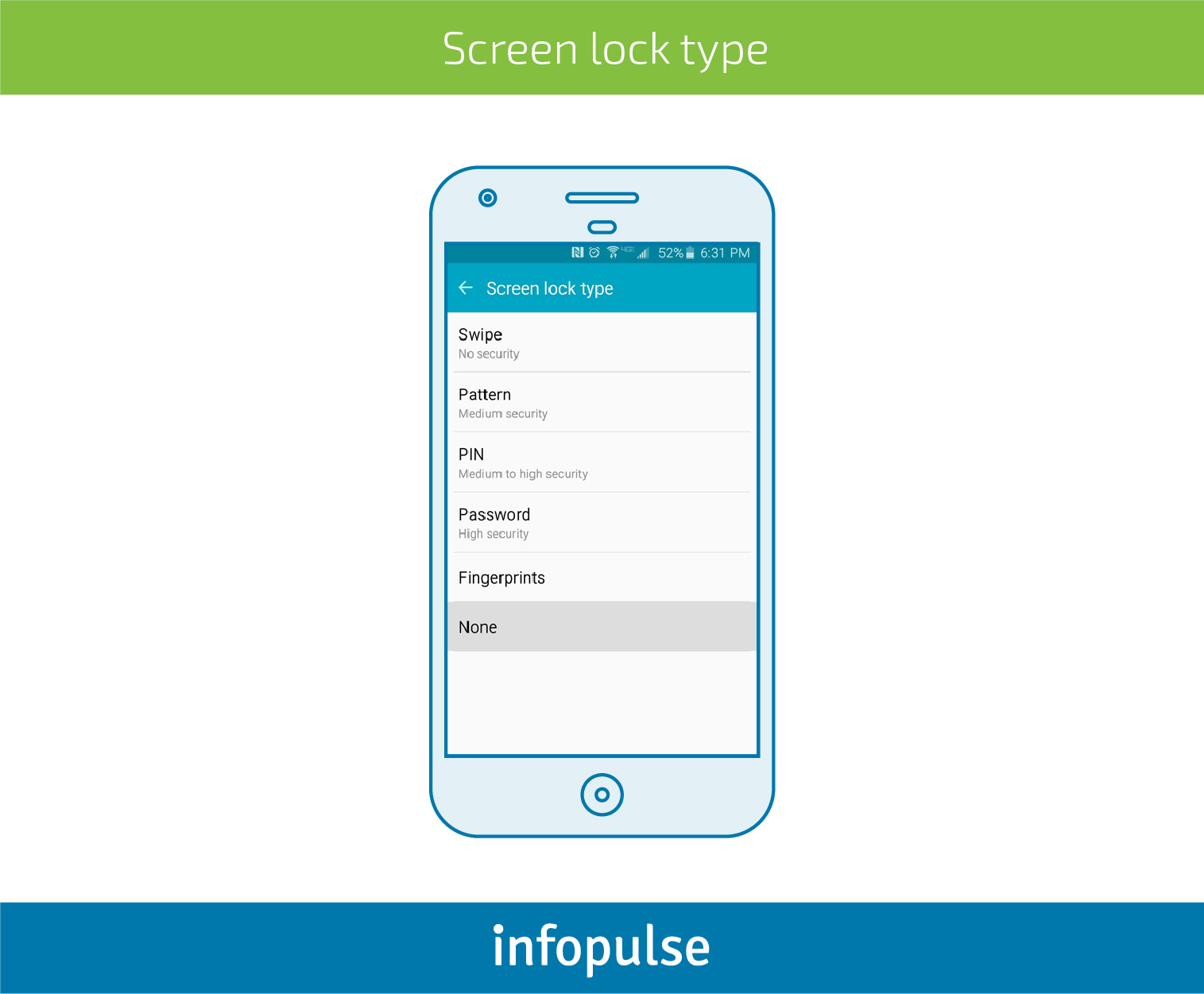
The fact that patterns are less secure against onlookers than passwords or PINs has been also confirmed by the security researchers from the US Naval Academy and the University of Maryland, who have come up with a simple explanation that the human brain can remember patterns better than digits with letters.
Another study reports that a hacker can also crack the pattern to your phone by taking a video of your fingers swiping on the screen from almost 2.5 meters and applying computer vision algorithm to identify “fingertip movement trajectory”. The researchers from three world-famous Universities hacked 95% of over a hundred patterns in five attempts. Hence, in terms of locking and unlocking a device, the security rate of a pattern could be described as “low to medium”.
PIN Code
Comparing a PIN code to a pattern, we cannot claim that a good hacker will not be able to crack your phone also using video and computer vision algorithm. However, Microsoft has recently reported that their TPM (crypto processor) chipped PIN code can be even better than a password implemented in Windows 10 and Windows 10 Mobile. Their main point is that such PIN is keyed to a particular device whereas a password is transmitted to the server and thus, can be compromised in the interim of a communication. MS PIN is flexible and can be turned in a password regarding its length and complexity. Besides, such PIN is an obligatory option to be able to switch to biometrics in Windows Hello. Yet, the problem of PIN security is still under a question since it is not backed up with another authentication factor.
Password
We have accustomed to the fact that a four-digit PIN is less safe than a strong password. However, the length and complexity of a password cannot provide the highest level of protection. For instance, 14-character alphanumeric password is possible to crack in about 160 seconds by the use of rainbow tables.
The need to strengthen password protection created different factors of authentication such as 2FA, 3FA, 4FA, and multi-factor authentication.
Multi-Factor Authentication
Multi-factor authentication is a confirmation method that permits a user to access an application only after he successfully presents 2 to 3 factors (evidence) successfully confirming his/her identity.
Multi-factor authentication can be based on a variety of protocols including Kerberos, which is used for authentication and secure data transmission in an open distributed network. Highly secure systems can utilize MFA authentication and OTP (one-time password) in a Kerberos protocol to establish reliable communication and verification channel between a client and a server.
The nature of authentication factors can be different but the main purpose of each should be to verify the identity of a user. The most common factors are connected to three categories:
- Knowledge factor is verification of what user knows, e.g. a password, a secret phrase, or an answer to the previously agreed question, etc. A PIN code is also used as an additional authentication channel, e.g. mobile applications for banking. Of course, it has certain limitations for a corporate network, namely the user’s phone becomes an insecure intermediary to the sensitive data of a company.
- Possession factor is verification of what a user obtains (logical or physical token), e.g. a software-based token that generates a one-time password, a key or certificate encrypted on the smartphone, a SIM card in the phone, ID card, etc.
- Inherence factor is verification of the user’s physical characteristics called biometrics, e.g. fingerprints, facial recognition, voice recognition, retina or iris scanning, etc.
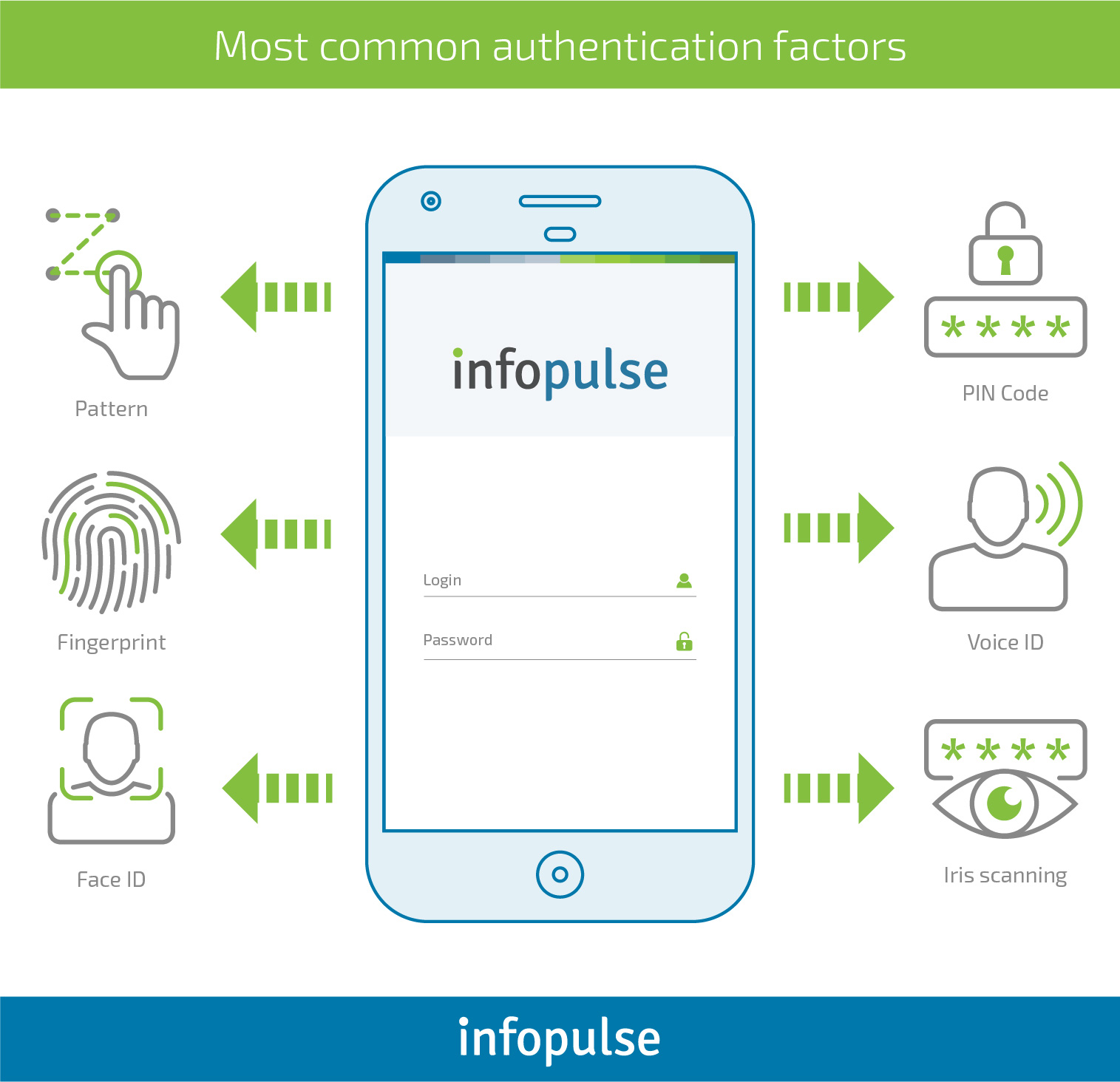
The implementation of an inherence factor in mobile applications greatly increases the security of logins and passwords and attracts more users to purchase an app with the integrated biometrics.
The following points represent currently applied factors.
Touch ID / Fingerprints
It is a well-known fact that any person possesses unique fingerprints primarily used by dactylography (a scientific study integrated with a criminal investigation to authenticate the person’s identity). However, with the arrival of new technologies, biometric authentication has become a mainstream method to safeguard the integrity of data through secure verification. Governmental organizations and enterprises have begun to widely implement fingerprint scanners for electronic voting, entering buildings and rooms instead of ID cards, online payments, sales operations, e.g. paying a subscription fee, SIM registration, customer onboarding, and validation of employees’ identities accessing corporate computer and other devices.
Another implementation approach has appeared with an in-built fingerprint reader in a smartphone. The much-talked-of fingerprint sensor Touch ID of iPhone 5S was the first to solve some major authentication problems, e.g. shoulder surfing of passwords when a user unlocks a phone in a crowd and phone hacking after the phone is stolen.
In 2017, the popularity of iPhones among consumers has reached 216 million of sold units worldwide. Although we cannot refer these figures to Touch ID solely, still the consumers’ interest to fingerprint biometrics has urged other manufacturers like Samsung, Google, LG, Sony, HTC, Huawei, etc. to implement this method in their models, e.g. Samsung Galaxy S8.
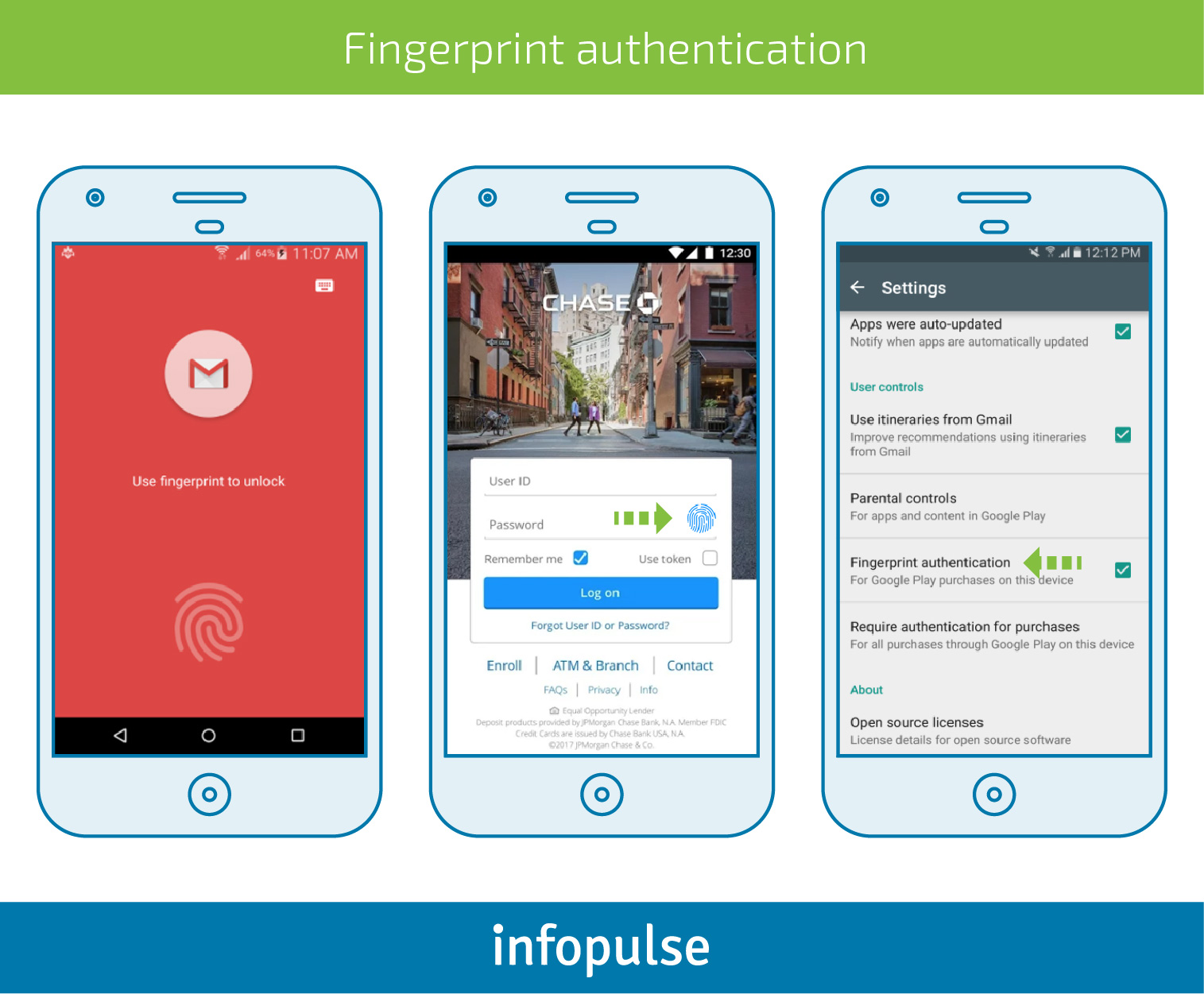
The success of a fingerprint scanner has been further implemented in mobile applications. Today you can open your Gmail or any messenger using a fingerprint instead of the alternative password or pattern lock. Moreover, modern smartphones with the integrated fingerprint sensor allow users to authenticate their app and game purchases in Google Play Store or make a transaction via one of banking apps (e.g. Bank of America, Chase, etc.) or bill payment systems (Mint Bills, Robinhood, etc.).
However, there are some apparent disadvantages of fingerprint biometrics considering safe authentication:
- Lack of accuracy since a fingerprint sensor is prone to false acceptance or false rejection;
- High chances of biometrics data security breaches and examples of fingerprint theft;
- High costs for maintenance of a fingerprint database;
- Necessary integration with a complex security program.
Face ID
The face recognition technology is enabled by the front camera, facial 3D map, and infrared image. A good example to demonstrate how it works is to view Face ID unlock feature of a much-talked-of iPhone X. Its front camera projects 30,000 dots on the person’s face to make a unique and accurate geometry-based pattern. The infrared camera that also catches an image to identify a person in any lighting and adapt to daily changes in the person’s appearance (make-up, glasses, hat, beard, etc.) reads the pattern and sends it to the neural engine. Then, images are transformed into a mathematical representation to match it with the initial facial pattern of the user.
Although the advanced technology behind Face ID allows being recognized from any angle and in total darkness, it still requires refinement. There were some cases of failed recognition when the camera distinguished close relatives and other unrelated people of the same race as owners of the identical face. Perhaps, the algorithm behind the technology was less tested to discern all existing races.
Hence, these crucial gaps mean that Face ID cannot fully substitute 2F authentication and function as a single authentication factor.
Blockchain-based authentication
Blockchain is a distributed ledger of any transactions built on the consensus mechanism. A record in this network can contain any kind of information. The stored data has no single location because a database is shared and constantly reconciled by the parties that do not need to trust each other. A third party or central unit is no longer needed to control transactions since data is distributed and hosted by all network users at the same time.
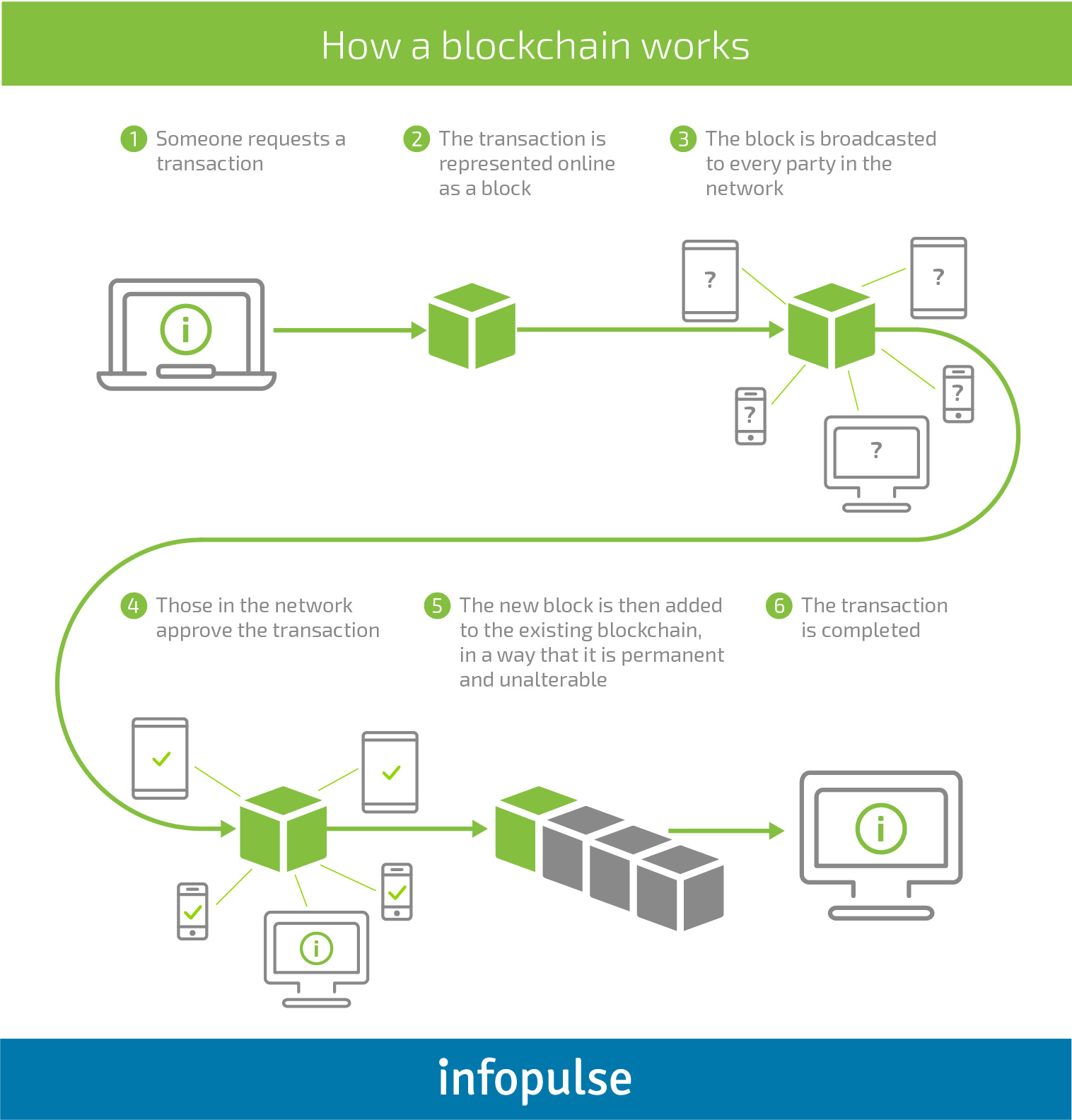
The security of contained data in each block of the ledger is ensured by the hash function. The hash is a unique fingerprint of a block and any changes in the block of information will change the hash too, which, as a result, will belong to a newly created block. Besides, each block also contains the hash function of a previous block connected to the ledger. Hence, the blockchain network is distributed, public, and transparent to each participant whereas the maintained data is impossible to alter or edit.
The blockchain technology has a variety of possible applications. Authentication is potentially the most interesting area since blockchain can totally transform the login system.
At the moment, Sony Corporation is aiming to build a blockchain-based authentication system by combining standard MFA procedure (a token generates authentication code) with two different blockchain-based platforms. According to the published patent, one blockchain platform would generate the codes and another would validate the user’s ID.
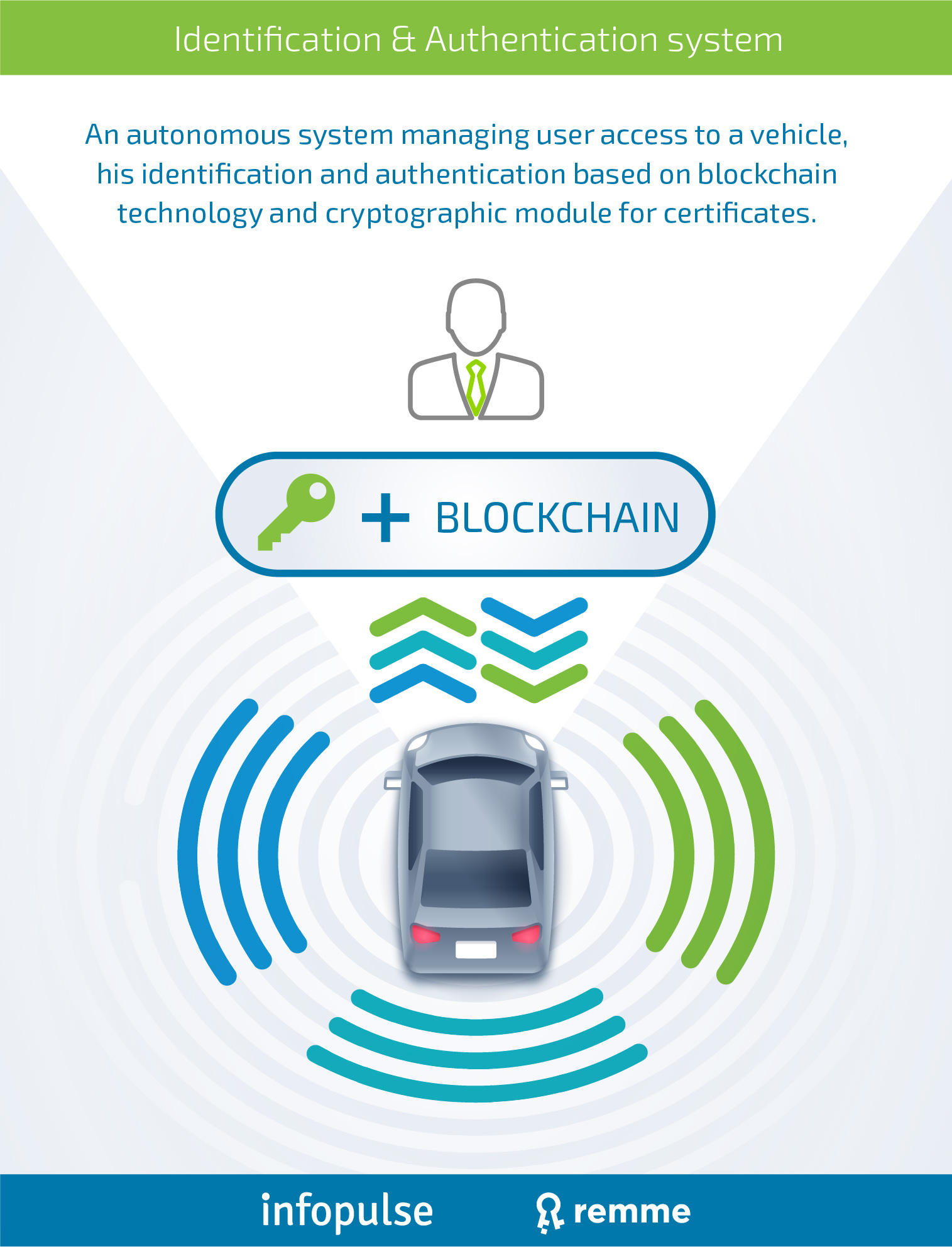
Another good example is a passwordless user authentication system that protects any vehicle’s network developed by Infopulse and REMME. It can be also potentially implemented in mobile applications. The access is safeguarded by a certificate in the hardware key obtained by the owner. The hardware key can create the mesh connection to a car to control it remotely with the help of SSL/TLS connection. After creating such connection, the car can check the revoked state of the certificate key with the Blockchain internal light node. This solution allows a car owner to securely share an access to the vehicle with any family member, another driver, a technician, etc. for a certain period of time in particular area or distance.
Conclusion
Summarizing the main points of the article, the multi-factor authentication (MFA) demonstrates more strengths than other possible methods due to its complexity and almost foolproof factors to identify a user. All biometrics types, despite their promising perspectives, still require improvement and additional testing to be able to replace the existing authentication mechanism completely. Therefore, currently, biometrics can supplement MFA as another authentication factor additionally securing the verification process.

![Power Apps Licensing Guide [thumbnail]](/uploads/media/thumbnail-280x222-power-apps-licensing-guide.webp)
![How to Build Enterprise Software Systems [thumbnail]](/uploads/media/thumbnail-280x222-how-to-build-enterprise-software-systems.webp)
![Super Apps Review [thumbnail]](/uploads/media/thumbnail-280x222-introducing-Super-App-a-Better-Approach-to-All-in-One-Experience.webp)
![ServiceNow and Third-Party Integrations [thumbnail]](/uploads/media/thumbnail-280x222-how-to-integrate-service-now-and-third-party-systems.webp)
![Cloud Native vs. Cloud Agnostic [thumbnail]](/uploads/media/thumbnail-280x222-cloud-agnostic-vs-cloud-native-architecture-which-approach-to-choose.webp)
![DevOps Adoption Challenges [thumbnail]](/uploads/media/thumbnail-280x222-7-devops-challenges-for-efficient-adoption.webp)
![White-label Mobile Banking App [Thumbnail]](/uploads/media/thumbnail-280x222-white-label-mobile-banking-application.webp)

![Mortgages Module Flexcube [Thumbnail]](/uploads/media/thumbnail-280x222-Secrets-of-setting-up-a-mortgage-module-in-Oracle-FlexCube.webp)
![Challenges in Fine-Tuning Computer Vision Models [thumbnail]](/uploads/media/thumbnail-280x222-7-common-pitfalls-of-fine-tuning-computer-vision-models.jpg)